In this tutorial you are going to learn about Binary Synchronous Communication Protocol in Computer Networks. It is also known as BSC protocol or BISYNC. You will learn about the byte-oriented approach, byte-oriented protocols, frame format of BISYNC and character stuffing in BISYNC protocol.
Byte Oriented Approach
In a byte-oriented approach, every frame is viewed as a collection of bytes or characters. Since it is dealing with characters, it is also known as character oriented approach.
We have basically three protocols:
- BISYNC - Binary Synchronous Communication Protocol
- PPP - Point-to-Point Protocol
- DDCMP - Digital Data Communications Message Protocol
Here, we are going to talk about BISYNC, which is the Binary Synchronous Communication Protocol.
BISYNC
BISYNC is a data link layer protocol that follows a sentinel approach. Sentinel approach means a guarding kind of behaviour will be there. The BISYNC protocol was developed by IBM. It is also preferred as BSC. Some experts refer BISYNC protocol as BSC and some experts refer the BISYNC protocol to be BISYNC. BISYNC is a byte-oriented protocol.
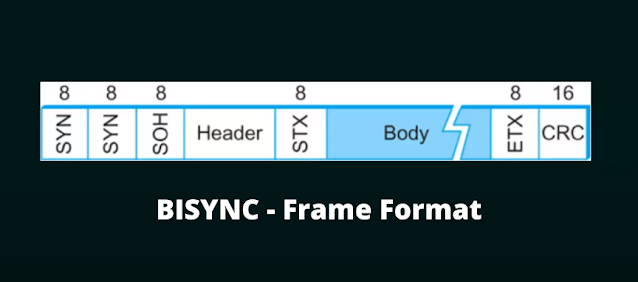
BISYNC - Frame Format
The frame format of the BYSINC includes, the starting one will be synchronous field which is of eight bits. The name says that it is BISYNC - BI means two, SYN means the special starting character is SYN and C stands for communication. Two synchronous fields in the starting of the frame. So if the frame format includes, the first SYN field of eight bits and the second SYN field of eight bits. This is the speciality about this BISYNC frame. These two fields are required, for identifying the start of the frame.
The third field includes the start of the header. The start of the header is also of eight bits. After the start of the header, it will be the header and after the header, we will have the start of the text, which is of eight bits. After the start of the text, we will have the variable length body and variable length body is followed by the end of the text. This end of the text is also of eight bits. And finally we will be having the last field which is the CRC. This cyclic redundancy check is for error detection and is of 16 bits.
Frame Format in Detail:
The frames that are transmitted will be starting from the leftmost side because this is the starting point.
- The beginning of a frame is denoted by sending a special SYN or a synchronized character which is repeated twice.
- The data portion of the frame is contained between special sentinel characters, STX that is the start of text and ETX which is the end of text. This data part is guarded by two fields that is the start of the text and the end of the text. The start of the text is of eight bits and the end of the text is also of eight bits.
- SOH: Start of the Header - It is of eight bits, then it is followed by the header field.
- DLE: Data Link Escape.
- CRC: It is cyclic redundancy check, which is mainly for error detection.
Now the problem is, we know it is a sentinel approach which means it is going to guard something. So the body is going to be guarded by the STX and the ETX fields and the header is also having the start of the header. But the problem is, we have a eight bit pattern in the start of the text and a eight bit pattern in the end of the text.
What if, the start of the text pattern or the end of the text pattern appears in the body and the receiver misunderstands that, it is the end of the text or the start of the text. This is a problem actually which is handled by character stuffing.
Character Stuffing
Character stuffing or Byte stuffing is the process of adding one extra byte, whenever there is a flag or escape character in the text. We will call this as the flag character. So whenever there is a synchronous character, twice if it is repeating in the body or the start of the text or the end of the text appears in the body, we are going to stuff one extra byte. Adding this one extra byte is done using DLE, which is Data Link Escape. So, character stuffing is done using data link escape in the BISYNC protocol.
This article on Binary Synchronous Communication Protocol (BISYNC) in Computer Networks is contributed by Rajnish Kumar. If you like TheCode11 and would like to contribute, you can also write your article to us. Here is our mail id - thecode11info@gmail.com

%20in%20Computer%20Networks.png)